A project that will involve some collaborative testing so I’m starting a separate thread for another sewing project here*.
We’re making faraday bags!
Making a what?
A faraday bag is for the main purpose of blocking unwanted RF signals from reaching an enclosed device. Either to secure a device from electronic surveillance or data leaks, a proper faraday bag will prevent a cell phone, laptop, etc. from sending or receiving wireless data. Personal comsec/sigint is one use case, evidence collection and storage for criminal investigations is another. For the purposes of securing a phone, this provides a simple means of carrying a phone around for use when you need it, yet keeping it ‘off the grid’ until you do.
It also provides HEMP protection for small and sensitive electronics, per a few testing standards we’ll get into later. No I don’t mean it’ll keep the drug dogs from finding your stash, wrong hemp. This one is about High-altitude ElectroMagnetic Pulse
I’ll leave it to some of the other great minds of this forum to perhaps chime in with why this is a useful bit of kit to have. If you’re on this forum however, there’s a good chance you already know.
Can’t I just turn the phone off?
No. That really stops nothing from being tracked with the state of modern cell phones these days. It will just kneecap your own ability to get any use out of it in the meantime.
So is this like an absurdly overbuilt talisman like a “crystal that protects your chakras from the 5G’s”?
No, they’re not. Or should I say, mine won’t be. The sad state of online knowledge about protecting equipment and organic bodies from the damaging effects of HEMP, RF exposure, and lightning strikes is that its filled with preposterously absurd amounts of bullshit. Even for the internet. Countless bizzare old-wives-tales exist everywhere on the topic from supposedly legit product marketing, to even most amateur radio forums. I see the most demonstrably false claims about what protects what from lighting/EMP damage on the HAM radio forums from people who supposedly have a scientific background and/or have at least read the ARRL radio handbook.
I make no claims to being an expert on the subject, but I do read the books by those that are. ‘The Grounds for Lightning and EMP protection’ by Polyphaser is a terrific primer on the topic of how to lightning proof a radio tower; it also covers how a lightning strike behaves, how and why the surge propagates through the ground and nearby conductive materials, as well as the similarities and significant differences in the mitigation required for lightning strikes vs an EMP.
Anyway, I’m way off track here. My point is that garbage data on the subject exists everywhere, and sorting the legit, standards-tested engineering practices from slick-marketed talisman salesmen is a chore.
So what are you building again?
Right, the faraday bags! I’m calling mine ‘Sigkill’ bags if only because its the first amusing term about them that came to mind. These will be cellphone and laptop pouches made from TitanRF Faraday Fabric made by MOS equipment. Other brands of faraday fabric exist and they’re probably functional, but this is one of the few I’ve found that was supported by actual testing standards and data about proper design practices to use the stuff effectively.
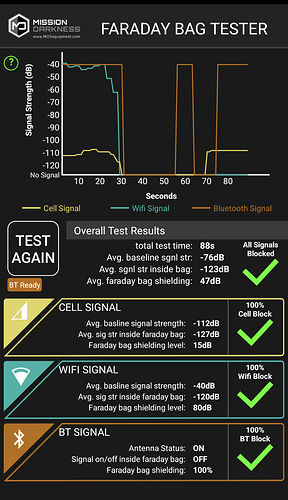
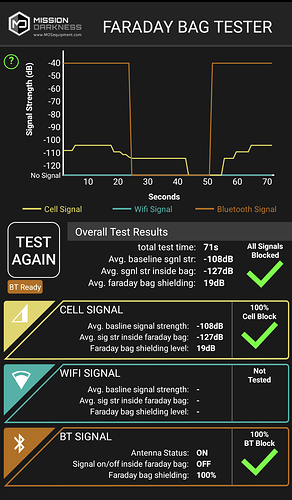
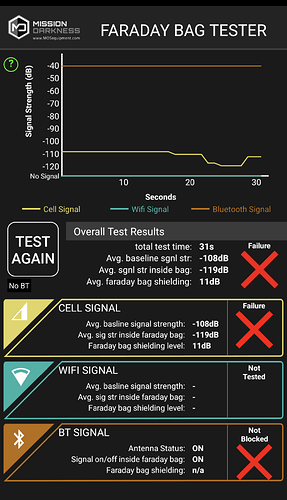
Current plan is to do some quick and dirty testing with the materials and a bunch of binder clips, then proceed to make a couple cell-phone sized bags with 3-layers of the faraday fabric, combined with a hyperD300 waterproof outer layer and a soft ripstop nylon lining for scratch protection of devices. The rest of the materials I need just arrived yesterday so, actual test reports coming soon!
* Pun intended and you can’t prove otherwise.